Thomson Reuters Authenticator mobile app installation and permissions
The Thomson Reuters Authenticator mobile app is used to confirm your account via multi-factor authentication (MFA). When you enable MFA for your account, you will need to download the app to your mobile device and approve the requested permissions.
Video: Installing Thomson Reuters Authenticator on Apple iOS devices (approx. 2 minutes)
Video: Installing Thomson Reuters Authenticator on Android devices (approx. 2 minutes)
Download and install the app to your mobile device
The steps to download and install the Thomson Reuters Authenticator vary depending on your device's operating system.
- On your iOS device, tap the App Store icon on your home screen.
- In the App Store, tap the Search button and enter "Thomson Reuters Authenticator" in the search bar.
- After locating the app, tap the Install button on the app's page, then follow the prompts to download and install the mobile app on your device.
- Once the installation is complete, the Install button changes to Open. Tap Open to launch the Authenticator app on your mobile device.
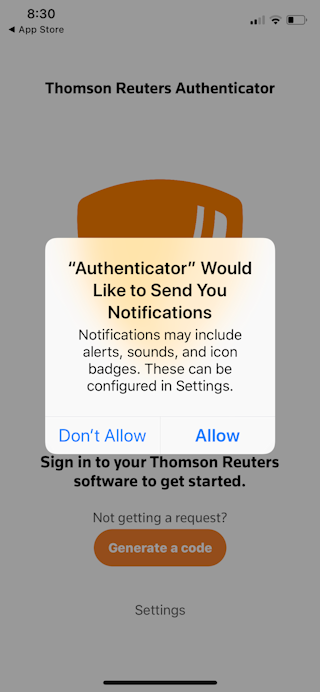
- The app displays an "Authenticator would like to send you notifications" prompt. Tap Allow to enable this permission, which allows the Authenticator app to display sign-in requests on your device.
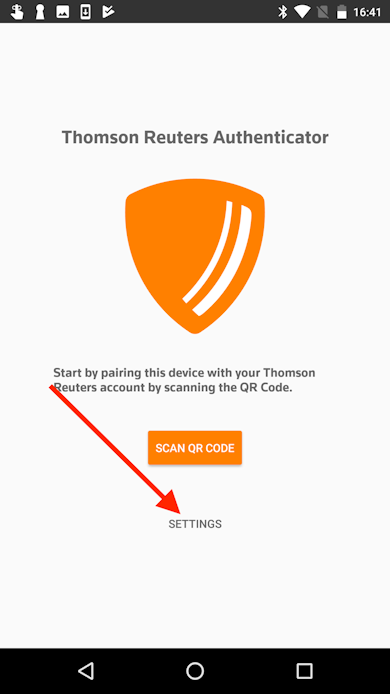
- With notifications enabled and the app open, you are ready to add an account. Tap Settings and then tap Add an Account.
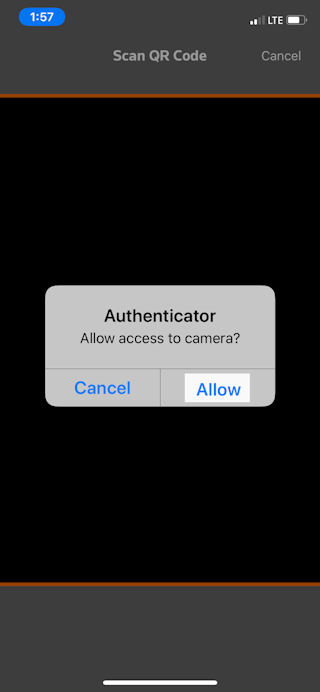
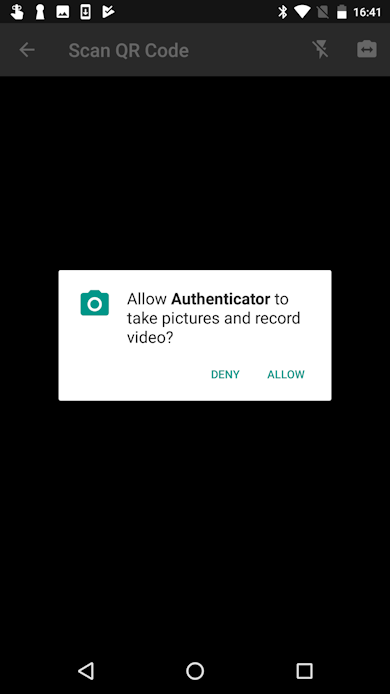
- The app displays a prompt requesting access to your device's camera. Tap Allow to enable this permission, which enables the Authenticator app to scan the QR code that's necessary to pair your device with your account.
- Once the app is installed and notifications and camera permissions are enabled, complete the setup wizard to enable security for your account and pair your mobile device with your login credentials.
- On your Android device, tap the Play Store icon on your home screen.
- In the Play Store, tap the search button and enter "Thomson Reuters Authenticator" in the search field.
- After locating the app, tap the Install button on the app's page, then follow the prompts to download and install the mobile app on your device.
- Once the installation is complete, the Install button changes to Open. Tap Open to launch the Authenticator app on your mobile device.
- In the Authenticator app, tap Settings and then tap Add an Account.
- The app displays a prompt requesting access to your device's camera. Tap Allow to enable this permission, which allows the Authenticator app to scan the QR code that's necessary to pair your device with your account.
- Complete the MFA setup wizard to set up MFA for your login and pair your mobile device with your login credentials.
Note: The timing and wording of the permissions prompts varies depending on the type of mobile device, your device's operating system, and the version of the mobile app. The required permissions are described below.
Permissions requested by the mobile app
The Authenticator app needs the following permissions to send login confirmation requests so you can verify your account when you have MFA enabled.
- Camera: This permission grants access to your device's camera, which the mobile app uses to scan the QR code during MFA setup. Once you've completed MFA setup, you can disable this permission.
- Network: This permission grants access to send and receive network traffic, so the mobile app can receive sign-in requests and send your approval, enabling you to log in to your software or website account.
- Notifications: This permission grants access to your mobile device's notifications, which enables the Authenticator app to display sign-in requests on your device.
- Prevent device from sleeping: On Android devices, this permission enables the mobile app to illuminate your device's screen and display push notifications, and does not prevent your device from entering a low-power standby mode.
The Thomson Reuters Privacy Statement encompasses all the products and services we offer. As such, some portions of the privacy statement are applicable only to specific products and services. If a product or service collects or processes Sensitive Personal Information, we handle such data in accordance with applicable laws. Thomson Reuters would not handle Sensitive Personal Information unless the client entered the personal information into our software or systems themselves, or with proper consent obtained where necessary to handle.

 Show expandable text
Show expandable text Hide expandable text
Hide expandable text